
- Overview
- Realm setup
- Active Directory & SCCM setup.
- Active directory - Security group
- Active directory - Broker account
- SCCM - Deployment collection
- SCCM - Administrative category for applications
- SCCM - Administrative category for office
- SCCM - Limiting collection for collections
- AD - Parent AD group for AD group list
- AD - Staging OU
- SCCM - Configuration directory
- SCCM - WinPE boot image setup
- Configuration tool & File
- Realm secret key
- Allowed WinPE instances
- Network access account
- Notification account
- Hostname formatting
- Automatically identify hostname
- Overrides
- Active directory staging OU
- MBAM Server details
- SMTP server details
- Notification types
- User state migration (USMT)
- Logs and Profiles location
- Disk setup
- Content availability check
- Error adding collection member
- Error adding AD group member
- Wait for Bitlocker decryption
- Approved hardware
- Extension Attributes
- Using sccmtspsi (Operator view)
- Task sequence steps
- Task sequence error codes
- sccmtspsi error codes
3.1.Active directory - Security group
The Realm security group serves two objectives.
- Acts as the gate keeper, by maintaining a list of Active Directory users who can access a SCCMTSPSI Realm instance.
- Provides read access into the configuration directory for a Realm.
Create the below Active Directory global security group.
sccmtspsi-users-XXX [Where XXX is the Realm name]
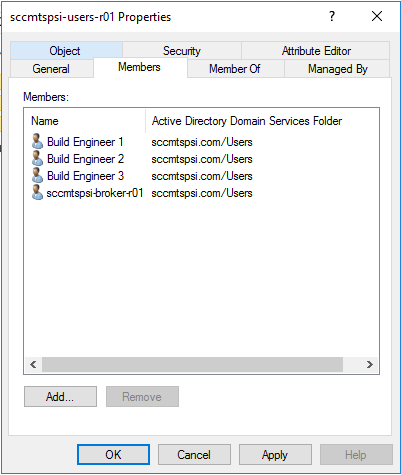
The security group members tab will look similar to the below image. Where “Build Engineer 1” , “Build Engineer 2” and “Build Engineer 3” are normal sccmtspsi operators and “sccmtspsi-broker-r01” is the broker account [discussed in the next section].
Note:
- The Realm security group can be a nested group. But for performance purposes, we recommend using a flat membership structure.
- Do not add any foreign security principals as a member of this group.